How AimBetter revealed a hacking attempt that the company’s cyber security tools did not detect.
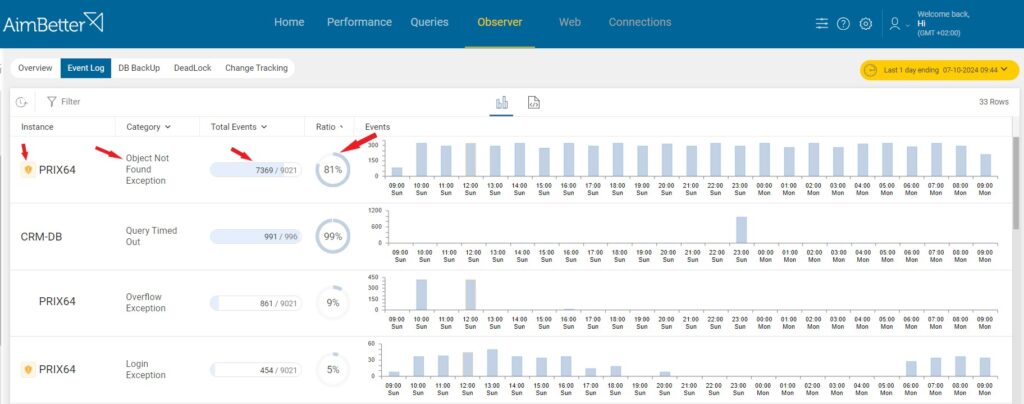
A large importer of electronic appliances recently faced a silent, yet potentially dangerous hacking attempt that went undetected by traditional cybersecurity tools. The company began receiving an unusual alert about recurring “Object not found” events. Concerned about the frequency of these alerts, the IT Manager turned to AimBetter’s Observer tab, which consolidates events with potential security, data loss, or consistency impacts. To his surprise, over 80% of the flagged events were “Object not found” occurrences.
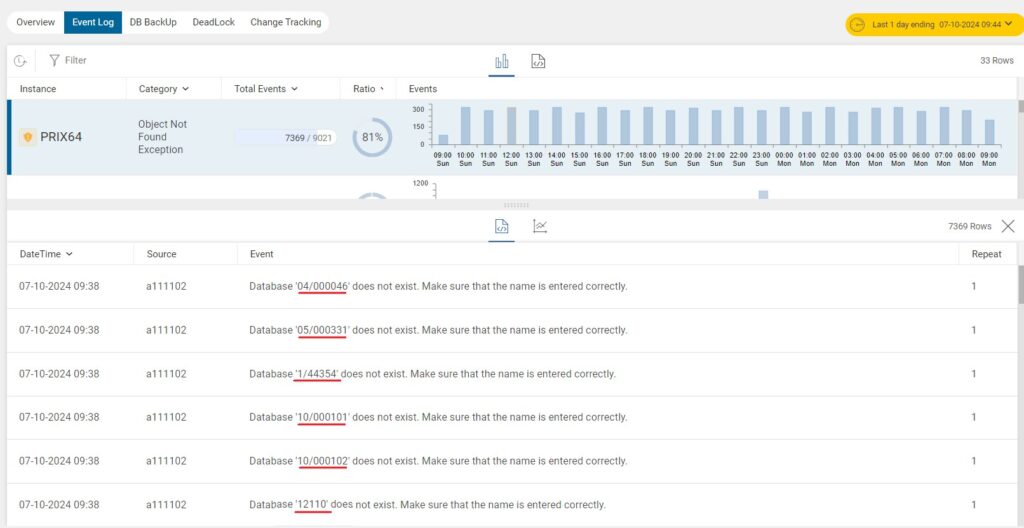
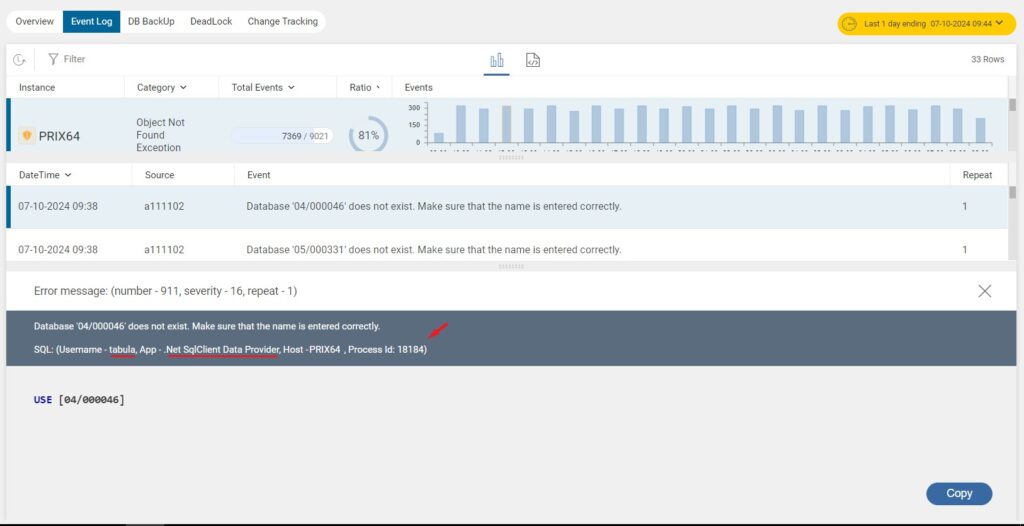
Upon further investigation, the IT Manager discovered something alarming: more than 7,000 of these events occurred within a single day, and all were related to a database that didn’t exist. Even more peculiar, the database name changed each time the event occurred, but the process ID remained the same across all instances.
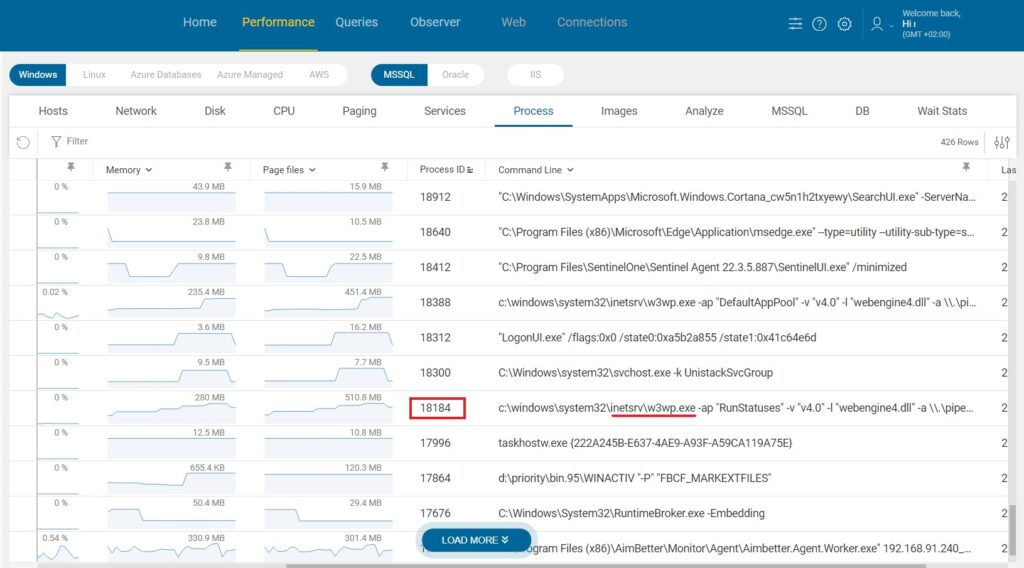
By focusing on this process ID, the IT Manager used AimBetter’s Processes tab to trace the origin of the activity. He found that the process was linked to the IIS (Internet Information Services) web server, a critical component of the company’s infrastructure that handles requests for web-based applications.
The hacker gained access using an existing login, possibly through an SQL injection vulnerability—a method that bypasses authentication controls and exploits vulnerabilities in database queries.
A deeper search revealed the manager’s suspicion that this was not just a benign error but part of a hacking attempt targeting the web server. By exploiting a vulnerability, the attacker generated thousands of error messages related to nonexistent databases, likely probing for weaknesses or trying to overload the system to find an entry point. The solution was immediate—patching the IIS web server to close the vulnerability and stop the attack.
So, you might wonder, how did the cyber security tools miss this one? Well, it’s a classic case of hackers being sneaky. Most traditional security tools are designed to detect big, obvious threats—like malware or brute force attacks—but this one flew under the radar because it didn’t set off those typical alarms. Instead of doing something super aggressive, the hacker was messing around with non-existent databases (kind of like a “phantom menace” of attacks).
The attacker also leveraged an existing login, which allowed them to fly under the radar of tools primarily designed to detect external intrusions or brute-force login attempts. Techniques like SQL injection enable hackers to manipulate databases through trusted access points, which most standard tools are not optimized to detect at the application level.
Traditional cybersecurity tools often operate in silos, focusing on network traffic, authentication attempts, or malware detection. AimBetter, by contrast, digs into the inner parts of the database server, identifying patterns of abnormal system behavior.
By providing visibility into areas that other tools overlook, AimBetter was able to catch this attack early on, recognizing the anomalous behavior despite the hacker’s attempts to keep it subtle.
The investigation was conducted without needing an expert DBA or a specialized cybersecurity professional, who would have had to spend much more time sifting through thousands of logs. AimBetter empowered the IT Manager to resolve the issue quickly and efficiently, saving time and resources.
With AimBetter, the company avoided a costly investigation or incident response, as the tool identified the problem early and accurately—making it not only a powerful but also a cost-effective solution for proactive management and security.
If you want to learn more about how Aimbetter can enhance your IT management by preventing disruptions and speeding up recovery from unexpected events, please get in touch with us today!